|
Win32:Swen is a worm, spreading through e-mail, shared folders, Kazaa P2P network and IRC. It switches off antiviral and personal firewall software on the infected computers. It fakes the "From:" field in the infected e-mails. The worm length is 106496 bytes. Being runned, the worm copies oneself to the %WINDIR% folder (%WINDIR% is a system variable containing the name of the Windows folder. Usually C:\Windows or C:\WinNT.) as a randomly named file. It creates files named germs0.dbv, swen1.dat and %COMPUTERNAME%.bat (%COMPUTERNAME% is a system variable containing the computer name.) in the %WINDIR% folder. It searches for a number of antiviral and personal firewall programs on the infected computer and tries to stop the found programs. It does changes to the registry database:
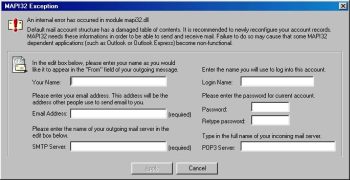
to the key HKEY_CURRENT_USER\Software\Kazaa\LocalContent. The running worm checks, if a registry database editor is runned. If so, the worm displays an error message and disables the editor. Periodically, "MAPI32 Exception Error" window is displayed. The window demands input of the mail account parameters - SMTP and POP3 server address, account name and password, user’s nickname. This is the MAPI32 Exception Error window: The worm sends oneself on the mail addresses found on the infected computer. The message parameters (“From:”, “Subject:”, message body, attachment name) are variable. The worm masks itself as security patch from Microsoft or as a returned undeliverable message. Only the attachment size is always same. The worm can use specially crafted creates MIME header, that on the MS Outlook Express versions with the MS01-020 bug enable it is runned automatically when the message is read. The worm copies oneself to the Startup folders on the shared disks. The worm searches for the folder with a IRC client on the infected computer and changes the file script.ini so the IRC client sends the worm copies to the users in the same IRC channel. If the Kazaa system is installed on the infected computer, the worm creates randomly named folder in the %TEMP% (%TEMP% is a system variable containing the name of the folder for temporary files store) folder and creates there multiple copies of itself with a different names. It shares the folder. Removal: avast! with VPS file dated on or after 18th September 2003 is able to detect this worm. Refer: Avast |

|

|
|